802.1X Port Security Commands auth-fail-action restricted-vlan Specifies the authentication-failure action for 802.1X multiple-host configurations. In an 802.1X multiple-host configuration, if RADIUS authentication for a Client is unsuccessful, traffic from that Client is either dropped in. 2 x HP ProCurve 1800-24G Managed Switches for failover. Which are both connected to the 2 HP ProCurves, (for failover). If we run everything without specific VMware VLAN configuration, (just VLAN config on the switches), all is good, but obviously if we want the VM instances to be in different VLANs, (on the same physical Dell box), we need. For example ip phone configuration. The other downside to 802.1X auth, it did not (originally) have support to pass back info to a switch to put a port 'tagged' into a vlan. RFC-4675 added that functionality, but Microsoft doesn't support it at all, I have been asking then for 2 yrs for it. ProVision ASIC switches from HP-ProCurve have. Hello, Trying to setup user based authentication on ports using 802.1x setup on 2610-48 procurve swicth. My config is: As I understood that when authentication enabled on win7 and passwrod is asked I need to provide operators password, since am not using RADIUS. Management and Configuration Guide ProCurve Switches Software Release F.01.xx (Refer to Release Notes for F.02.xx and greater) Series 2500 Switches.
How to enable RADIUS switch login authentication on an HP switch - This article provides a general overview of how to windows domain usernames and passwords to log onto your HP switch.
It assumes you have a basic knowledge of Microsofts implementation of RADIUS, Network Policy Server (NPS)
Switch configuration
Hp Switch 802.1x
Configure the radius server configuration on the switch (Configure the Microsoft NPS RADIUS server, with a matching key)
Put the following configuration on the switch
Windows NPS / RADIUS Configuration
Set up your RADIUS server to allow the auth requests
I normally create a group in Active Directory, called NetworkAdmins, and then add the users who will be maintaining the switches to that group..
Add the switch as a client to NPS - I like to prefix all my switches with SW- so that I can reference all switches when I create policies
Match the shared secret with the key you created on the switch earlier
Hp Procurve 802.1 X Configuration Example Sheet
And then the trickery to make it work, you are returning an attribute here.
Note, you may have to change the the source IP address, so that the switch sources the RADIUS requests from the correct IP address.
How to change the source IP address on an HP Provision switch
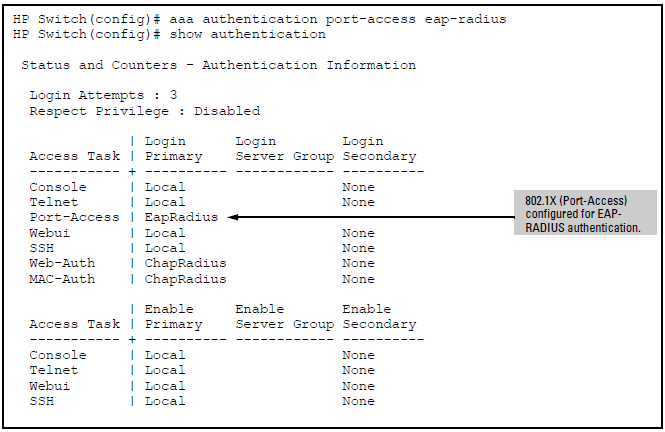
How to configure 802.1x Port Authentication on HP Procurve Switches, and MAC Authentication for HP printers.
It also allows Avaya handsets to bypass authentication requests.
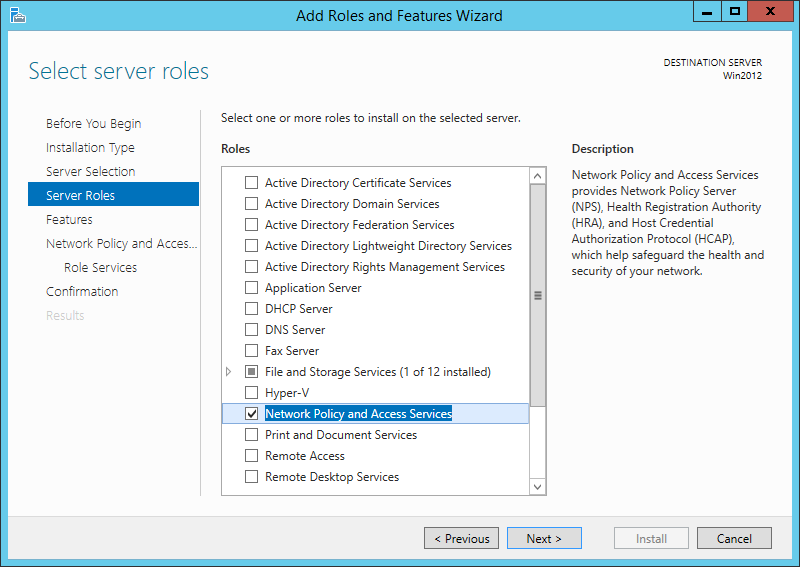
This guide shows you how to configure the network switch, and Microsoft NPS server configuration for the automatic 802.1x authentication of PC's and MAC authentication for other devices

It assumes you already have the Microsoft NPS server installed, and it also assumes you have a PKI already installed, and therefore a client certificate on those machines you want to enable 802.1x.... :)
First, plan out what VLAN you want to assign as your 'Authenticated' VLAN, and what VLAN you want to use as your 'Unauthorised VLAN'. Make sure you have DHCP running in both VLAN's, and first plug your laptop into an untagged port in both VLAN's to make sure that you can get an IP address / access the internet or other resources you expect
This example uses the following:
User Authenticated VLAN = 10
Printer Authenticated VLAN = 5
Unauthorised VLAN = 20
Voice VLAN = 15
RADIUS Server = 10.10.10.10
Client PC Configuration
Unlike the wireless network card, the wired authentication service is disabled by default, so you must enable it on every PC. Make sure this is in your group policy if you want to enable it on all machines in your domain.
For an individual PC, click start / run and type services.msc
Change the Startup Type to Automatic, and then start the service
