Cracking WPA/WPA2 (handshake) with hashcat With hashcat, there is a possibily of various attack vectors. We could do a straight dictionary attack, brute-force attack, combinator attack or even masks attack, i.e. Making rules to find various possibilities of trying different characters at different positions. WPA Personal = WPA-PSK (and WPA2-PSK). Apple prefers to use the term WPA Personal, which is probably what you saw in the Airport documentation. From Wikipedia: 'WPA-Personal: Also referred to as WPA-PSK (Pre-shared key) mode, it is designed for home and small office networks and doesn't require an authentication server.
If you want to know how to hack WiFi access point – just read this step by step aircrack-ng tutorial, run the verified commands and hack WiFi password easily.
With the help a these commands you will be able to hack WiFi AP (access points) that use WPA/WPA2-PSK (pre-shared key) encryption.
The basis of this method of hacking WiFi lies in capturing of the WPA/WPA2 authentication handshake and then cracking the PSK using aircrack-ng.
How to hack WiFi – the action plan:
- Download and install the latest
aircrack-ng - Start the wireless interface in monitor mode using the
airmon-ng - Start the
airodump-ngon AP channel with filter for BSSID to collect authentication handshake - [Optional] Use the
aireplay-ngto deauthenticate the wireless client - Run the
aircrack-ngto hack the WiFi password by cracking the authentication handshake
1. Aircrack-ng: Download and Install
The Latest Version Only: If you really want to hack WiFi – do not install the old aircrack-ng from your OS repositories. Download and compile the latest version manually.
Install the required dependencies:
Download and install the latest aircrack-ng (current version):
Ensure that you have installed the latest version of aircrack-ng:
2. Airmon-ng: Monitor Mode
Now it is required to start the wireless interface in monitor mode.Monitor mode allows a computer with a wireless network interface to monitor all traffic received from the wireless network.
What is especially important for us – monitor mode allows packets to be captured without having to associate with an access point.
Find and stop all the processes that use the wireless interface and may cause troubles:
Start the wireless interface in monitor mode:

In the example above the airmon-ng has created a new wireless interface called mon0 and enabled on it monitor mode.
So the correct interface name to use in the next parts of this tutorial is the mon0.
3. Airodump-ng: Authentication Handshake
Cool Tip: Want to have some “fun”? Create a Linux fork bomb! One small string that is able to hang the whole system! Read more →
Now, when our wireless adapter is in monitor mode, we have a capability to see all the wireless traffic that passes by in the air.
This can be done with the airodump-ng command:
All of the visible APs are listed in the upper part of the screen and the clients are listed in the lower part of the screen:
Start the airodump-ng on AP channel with the filter for BSSID to collect the authentication handshake for the access point we are interested in:
| Option | Description |
|---|---|
-c | The channel for the wireless network |
--bssid | The MAC address of the access point |
-w | The file name prefix for the file which will contain authentication handshake |
mon0 | The wireless interface |
--ignore-negative-one | Fixes the ‘fixed channel : -1’ error message |
airodump-ng captures a handshake.If you want to speed up this process – go to the step #4 and try to force wireless client reauthentication.
After some time you should see the WPA handshake: 00:11:22:33:44:55 in the top right-hand corner of the screen.
This means that the airodump-ng has successfully captured the handshake:
4. Aireplay-ng: Deauthenticate Client
Cool Tip: Want to stay anonymous? Learn how to use PROXY on the Linux command line. Read more →
If you can’t wait till airodump-ng captures a handshake, you can send a message to the wireless client saying that it is no longer associated with the AP.
The wireless client will then hopefully reauthenticate with the AP and we’ll capture the authentication handshake.
Send deauth to broadcast:
Send directed deauth (attack is more effective when it is targeted):
| Option | Description |
|---|---|
--deauth 100 | The number of de-authenticate frames you want to send (0 for unlimited) |
-a | The MAC address of the access point |
-c | The MAC address of the client |
mon0 | The wireless interface |
--ignore-negative-one | Fixes the ‘fixed channel : -1’ error message |
Cool Tip: Need to hack WiFi password? Don’t wast your time! Use “John the Ripper” – the fastest password cracker! Read more →
5. Aircrack-ng: Hack WiFi Password
Unfortunately there is no way except brute force to break WPA/WPA2-PSK encryption.To hack WiFi password, you need a password dictionary.
And remember that this type of attack is only as good as your password dictionary.
You can download some dictionaries from here.
Crack the WPA/WPA2-PSK with the following command:
| Option | Description |
|---|---|
-w | The name of the dictionary file |
-b | The MAC address of the access point |
WPAcrack.cap | The name of the file that contains the authentication handshake |
Cool Tip: Password cracking often takes time. Combine aircrack-ng with “John The Ripper” to pause/resume cracking whenever you want without loosing the progress! Read more →
by hash3liZer . 18 November 2018
In this tutorial, we will automate the wireless cracking process using WiFite. Cracking wireless can exceptionally be tricky when it comes to automation for multiple Access Points. A device like Raspberry Pi could be more compact and helpful in any such cases. Consider a device which can be taken anywhere freely with a binded script in it to check for default/weak wireless passphrases.
WiFite :-
WiFite is an automated WiFi Cracking tool written in Python. It is basically a combination of various famous pentest tools like airmon, aircrack and reaver etc. It is widely used for cracking WEP and WPA (WPS) wireless networks. WiFite version 2 has been released and is likely to be already installed if you are running Kali or Parrot linux distros.
However, since i want this tutorial to be followed by the users of Raspberry Pi and Ubuntu as well, we will make a head-start installing installing WiFite.
STEP 1
WiFite Installation
The project is available on github: https://github.com/derv82/wifite2
Clone the repository using git:
Now, install some pre-requisities required for PMKID attack:
There are some of the required tools for WiFite to properly run and some others are optional. You can find this list on the link given above. The utilities iwconfig and ifconfig would already be installed. However, if you are running short of aircrack suite, that can be installed easily using apt package manager:
Now, to install WiFite:
This will install WiFite as a normal Linux command by creating a symlink to /usr/bin/ directory. You can verify it by printing the manual:
STEP 2
Hack Wifi Wpa Mac
Monitor mode
You would need you wireless card to be operating in monitor mode which can be done with airmon-ng:
STEP 3
WPA/WPA2 Cracking using handshake
The standard way being used by most of the scripts is to capture a handshake and compute the encoded keys to brute force the actual key. However, lately a new method was discovered which uses PMKID to accomplish the task. To Brute force WPA/WPA2 networks using handshake, run the below command:
Arguments:
- -i: Monitor mode interface to use.
- --random-mac: Randomize the Wireless Adapter MAC address.
- --clients-only: Target networks with stations only.
- --wpa: Target WPA/WPA2 networks only. WPS included.
- --dict: Wordlist to use for cracking MIC hash.
STEP 4
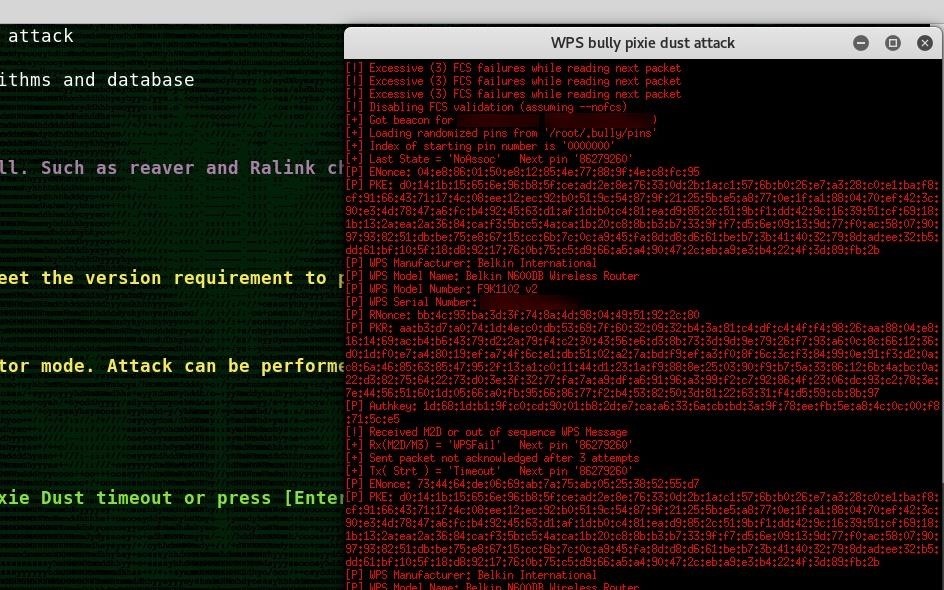
WPS Cracking
WPS protocol was developed to provide user with the ease of connecting to Access Points. Hownever, the protocol is itself vulnerable on a variety of misconfigured routers. WiFite uses pixie dust and WPS Pin attack against WPS networks. To only target wps networks:
Arguments:
- --nodeauths: Do not send deauthentication packets.
- --wps: Only target WPS networks.
- --wps-only: Only use Pin brute force and pixie dust attack.
STEP 5
WPA/WPA2 cracking using PMKID
Lately, a new method was discovered by Jen Steube for cracking WPA/WPA2. The difference in between handshake and PMKID is that handshake requires the whole 4-way handshake to compute the key to be bruteforced. However, with this new trick an attacker make the Access Point transfer the first EAPOL message which contains the key to be bruteforced. PMKID attack requires two more tools. Install hcxtools:
Hack Wpa Kali
Then install hcxdumptool:
To crack WiFi Networks using pmkid attack:
Arguments:
- --pmkid: Only use PMKID to crack wireless networks.
- --pmkid-timeout: Timeout for first Message to receive.
- --dict: Wordlist with passwords to brute force.
Hack Wpa Wifi On Mac
STEP 6
Cracking Networks
To see which networks are cracked, just execute this command:
Hack Wpa Macos
Conclusion
WiFite is an awesome wireless cracking tool which automates the cracking stuff using other pentest utilities. It can easily be integrated with a compact device like Raspberry pi and could be very useful tool for a number of reasons.
