FlexVPN is a framework to configure IPSec VPNs on Cisco IOS devices; it was created to simplify the deployment of VPN solutions of all type (Site-to-Site, Remote Access etc). It uses a common configuration template for all VPN types. FlexVPN is based on IKEv2 and does not support IKEv1.

In FlexVPN, what is the role of a NHRP resolution request?A. It allows these entities to directly communicate without requiring traffic to use an intermediate hopB. It dynamically assigns VPN users to a groupC. It blocks these entities from to directly communicating with each otherD. It makes sure that each VPNContinue reading. The First Cloud Remote Access. EZ VPN ™ gives you access to any of your remote network locations. Connect to your office and work remotely, manage your home automation devices, upgrade your industrial control panel, check your webcams, with EZ VPN ™ anything behind a firewall can be safely and easily accessed without even touching your existing network configuration. IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco's FlexVPN implementation. The Best Premium Unlimited VPN Proxy. PlexVPN has one repository available. Follow their code on GitHub. In this post I will also introduce two concepts that are frequently used in software development world - DRY and “Convention over Configuration”. This post is a precursor to the upcoming FlexVPN configuration post on Packetpushers. FlexVPN network overview FlexVPN topology will consist of two FlexVPN “clouds”. Each cloud has a Hub router and multiple Spokes. Each Spoke is connected to.
IKEv2 Features
- IKEv2 is more secure than IKEv1 because it supports the latest Suite B cryptographic algorithms
- Built-in support for Dead Peer Detection (DPD) and NAT-Traversal
- Is resistant to DoS attacks
- Consolidated IKEv1 main and aggressive modes into one method, called “initial”
- Supports more authentication methods; in addition to PSK, certificates it also supports EAP authentication.
- XAUTH not used in IKEv2, EAP is used for authentication instead: EAP Tunneling: EAP-TLS, EAP-PEAP, EAP-PSK, EAP Non-Tunnelling: EAP-MSCHAPv2, EAP-MD5, EAP-GTC and EAP Anyconnect
IKEv2 Message Exchange
IKEv2 has only two initial phases of negotiation: IKE_SA_INIT exchange and IKE_AUTH exchange.
IKE_SA_INIT
- The initial exchange, in which the peers establish a secure channel by agreeing IKEv2 Proposal.
- This happens un-encrypted
- The exchange contains 2 packets/messages – combines all the information from IKEv1 MM 1-4
IKE_AUTH
- Once IKE_SA_INIT exchange is complete all subsequent communication is encrypted
- IKE_AUTH authenticates the remote peer using the method specified in the IKEv2 Profile
- Once the peers have successfully authenticated the IPSec SA is established
CREATE_CHILD_SA (Optional)
- The CREATE_CHILD exchange is used if the IKE SA or one of the Child SAs needs to be re-keyed. This serves the same function as Quick Mode exchange does in IKEv1.
- Only 2 packets in the exchange, but will be repeated for every re-key or new SA.
IKev2 DoS Prevention
IKEv2 uses stateless anti-clogging cookies, which is used for protection of DoS attacks from spoofed source addresses. The initiator sends an IKE SPI to the Responder, who acknowledges the SPI sent and requests confirmation with a cookie specified. The responder will limit resources until the initiator responses with the correct cookie ID.
The anti-clogging cookies are optional Anti-DoS mechanism. They are exchanged in the first 2 messages in the IKE_SA_INIT exchange.
Configuration Components
The following IKEv2/IPSec configuration components are required for FlexVPN
| Component | Description |
| IKEv2 Proposal |
|
| IKEv2 Policy |
|
| IKEv2 Keyring |
|
| IKEv2 Profile |
|
| IPSec Transform Set |
|
| IPSec Profile |
|
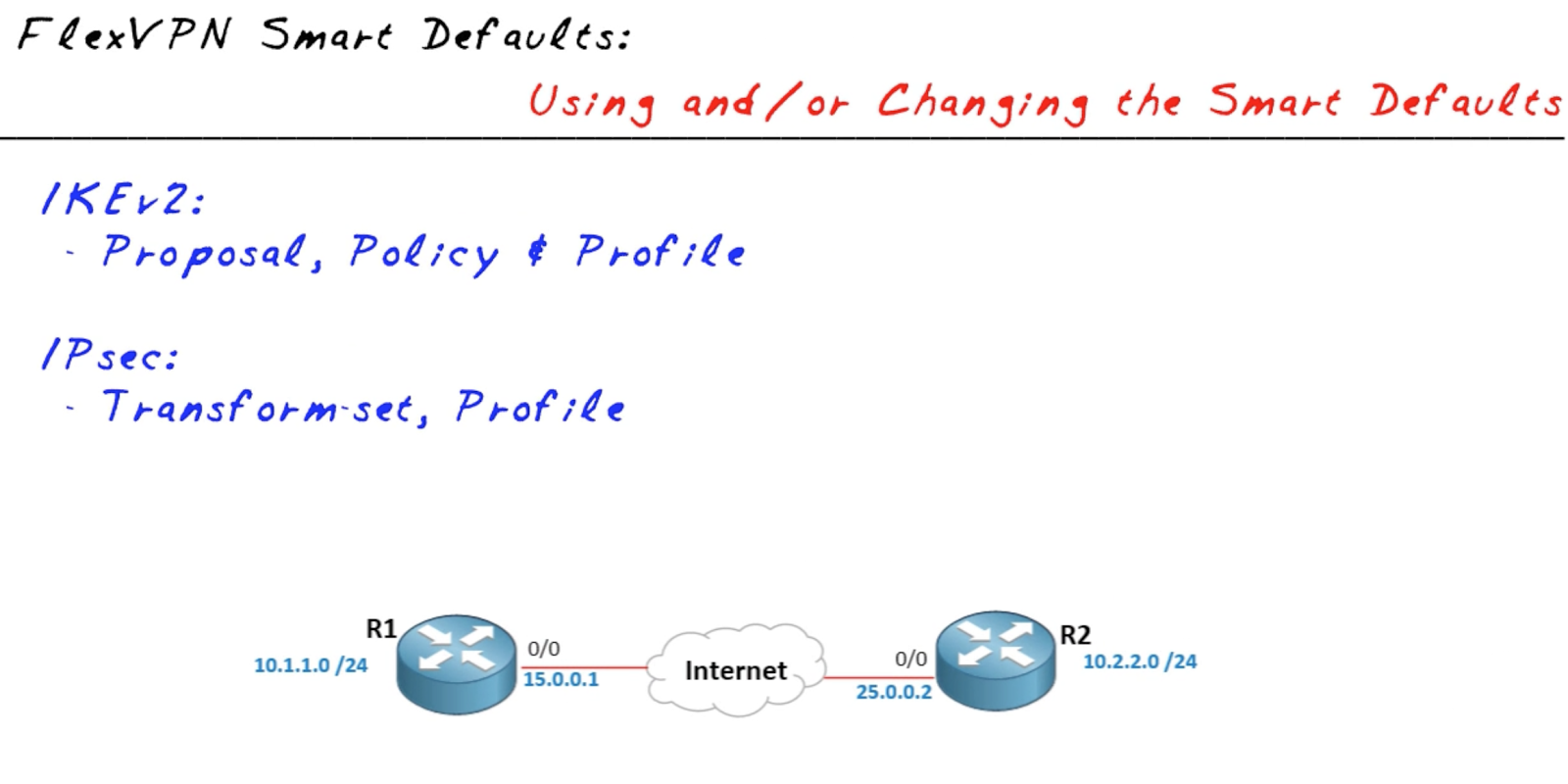
Smart Defaults
The FlexVPN configuration can be minimised using the IKEv2 Smart Defaults, these specify default values for all components except IKEv2 Profile and Keyring (if PSK used).
- Smart defaults can be modified if required
- Smart defaults will only be displayed in the running-config if you use the command “show running-config all“
- The default configuration can be disabled by using “no” before the command
- The default mode for the default transform set is “transport“, where as all other transform sets the default mode is “tunnel“
| Description | Show command | Default values |
| Transform Set | show crypto ipsec transform-set default | crypto ipsec transform-set default esp-aes 128 esp-sha-hmac |
| IPSec Profile | show crypto ipsec profile default | crypto ipsec profile default set transform-set default set ikev2-profile default |
| IKEv2 Proposal | show crypto ikev2 proposal default | crypto ikev2 proposal default encryption aes-cbc-256 aes-cbc-192 aes-cbc-128 integrity sha512 sha384 sha256 sha1 md5 group 5 2 |
| IKEv2 Policy | show crypto ikev2 policy default | crypto ikev2 policy default match fvrf any proposal default |
| IKEv2 Authorization Policy | show crypto ikev2 authorization policy default | crypto ikev2 authorization policy default route set interface route accept any |
The “IKEv2 Profile” will need configuring with Identity, Authentication method and keyring (if PSK used).
All defaults can be modified, deactivated or restored
| Modifying defaults | crypto ikev2 proposal default encryption aes-cbc-128 Integrity md5 crypto ipsec transform-set default esp-aes 256 esp-sha-hmac |
| Restoring defaults | default crypto ikev2 proposal default crypto ipsec transform-set |
| Disabling defaults | no crypto ikev2 proposal default no crypto ipsec transform-set default |
In the previous articles in this IKEv2 series, we have looked at how to configure LAN-to-LAN and FlexVPN Server and Client using IKEv2. In this article, we will be configuring another type of VPN called FlexVPN Spoke to Spoke, which is essentially DMVPN but with IKEv2.
The lab setup we will use in this article is shown below:
FlexVPN Server/Client
In the diagram above, we have two FlexVPN clients connecting to one FlexVPN server. Before we go to the FlexVPN spoke-to-spoke configuration, let us see what happens if we just use the standard FlexVPN server/client configuration. The configuration on the FlexVPN server is as follows:
The configuration on one of the FlexVPN clients is as follows:
Note: You can replicate the configuration for the other FlexVPN client; just remember to change the IP addresses (172.16.1.1 to 172.16.2.1 and 10.0.0.10 to 10.0.0.20) and the subnet matched under the FLEX_ACL.
If you look at the FlexVPN server configuration, you will notice that the FLEX_ACL permits any network. This basically means the FlexVPN server is advertising a default route to the clients. The FlexVPN server also sends the virtual-access interface address because of the “route set interface” command under the IKEv2 authorization policy.
When our tunnels are set up, we can see the routes advertised by the FlexVPN server on one of the FlexVPN clients:
If we check the routing table of the FlexVPN server, we will also see the networks advertised by the FlexVPN clients:
For testing purposes, let us check that the FlexVPN client can ping the FlexVPN server’s network, i.e., 192.168.10.1.
On the FlexVPN server, we can see that this traffic was encrypted/decrypted over the Virtual-Access1 interface:
Now, from a routing perspective, since the FlexVPN clients also have a default route through the tunnel (through the FlexVPN server), it means they will forward traffic to each other through that tunnel. For example, if FlexVPN client1 pings FlexVPN client2, the traffic will flow through the FlexVPN server.
I can verify that this traffic goes through the FlexVPN server by looking at the encrypted/decrypted section of the IPsec SAs again:
FlexVPN Spoke to Spoke
As with normal DMVPN, it is more desirable for spoke-to-spoke traffic to flow through a tunnel between the spokes themselves rather than going through the hub. This is what FlexVPN Spoke to Spoke helps us achieve and it also uses NHRP to achieve this functionality. However, unlike normal DMVPN, the NHRP configuration required for FlexVPN Spoke to Spoke is much simpler.
Looking at it from a high level, we can bring out the following requirements for FlexVPN Spoke-to-Spoke configuration:
- The configuration on the FlexVPN server (hub) will remain fairly the same, i.e., we still configure a dynamic VTI. However, some NHRP commands will be added under the VTI.
- The Spokes (FlexVPN clients) will still have a static VTI configured for Hub-to-Spoke communication. However, some NHRP commands will also be included under the tunnel interface.
- A dynamic VTI needs to be configured on the spokes so that they can dynamically build spoke-to-spoke tunnels. This third point is where FlexVPN Spoke to Spoke really defers from the normal FlexVPN server/client model.
There are three basic NHRP commands that we require for the FlexVPN Spoke-to-Spoke configuration:
- On both the hub and spoke, we need to configure an NHRP network ID under the VTI, which identifies the DMVPN cloud and also enables NHRP on that interface.
- On the hub, we need to enable NHRP redirect so that the hub can inform the spokes that they can communicate directly, i.e., trigger spoke-to-spoke tunnel negotiation.
- On the spokes, we need to enable NHRP shortcut so that spokes will forward traffic to other spokes’ remote subnets via the spoke-to-spoke tunnel.
Keeping these points in mind, let’s get down to the configuration. The configuration addition on the FlexVPN server (Hub) is as follows:
Flexvpn +ipv6
Note: You cannot make changes to a Virtual-Template configuration if it has associated Virtual-access interfaces; you will get the following error: “% Virtual-template config is locked, active vaccess present.” To make changes, clear your IKEv2 and IPsec SAs (and make sure they are not rebuilt by shutting down the physical interfaces, maybe on the clients).
The configuration addition on the FlexVPN Client1 is as follows:

Note: You can replicate the spoke configuration on the 2nd FlexVPN client with the necessary IP address change.
When the tunnels are up, Hub-to-Spoke traffic will still flow as normal:
Now what happens when we ping 172.16.2.1 (Spoke2) from 172.16.1.1 (Spoke1)?
Flexvpn Download
We see that the traffic is successful, but something actually happened behind the scenes: a dynamic tunnel was built. The ping traffic started off going through the hub but, after the dynamic tunnel was built, the remaining ping packets went over this dynamic spoke-to-spoke tunnel:
If we use the show ip nhrp command, we see the cache entries for the remote spoke and NHRP routes there:
You can refer to this Cisco document for details on how the NHRP redirect works to build FlexVPN Spoke to Spoke tunnels.
Summary
In this article, we have configured FlexVPN Spoke to Spoke, which allows spokes to communicate with each other over dynamically created tunnels.
I hope you have found this article insightful.
Best Vpn Service

Vpn For Beginners
References and Further Reading
Flexvpn Cisco
- Configuring FlexVPN Spoke to Spoke: http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_ike2vpn/configuration/xe-3s/sec-flex-vpn-xe-3s-book/sec-flex-spoke.html
